Governance.
Embedded.
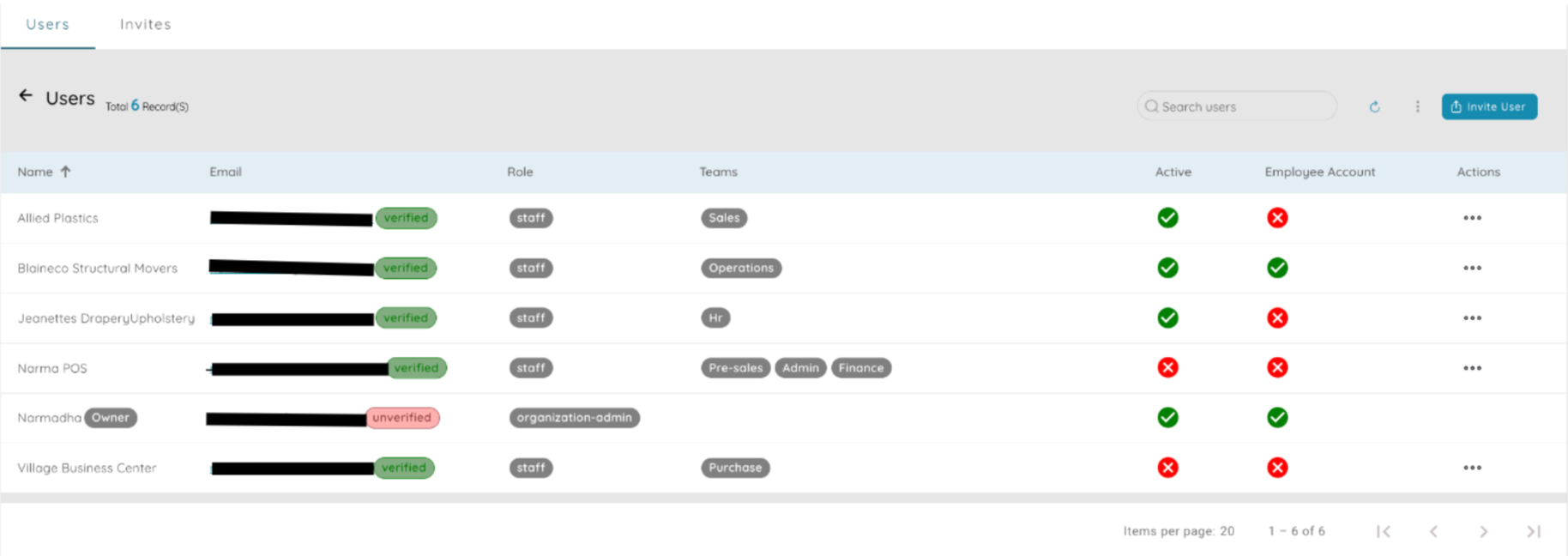
Role-based access. Multi-layer approvals. Complete audit trail. Security that scales with you.
Enterprise-grade security without the enterprise headaches. Your data. Your rules. Your control.
Security features that matter
- • Field-level security
- • Department restrictions
- • Time-based access
- • IP restrictions
- • Dynamic groups
- • Hierarchical approvers
- • Conditional approvals
- • Delegation

- • Timestamped logs
- • User ID
- • Change history
- • Export reports

- • Sequential
- • Parallel
- • Conditional routes
- • SLA tracking

Security in action




Built-in, not bolted on

Role-Based Access Control (RBAC)▾
Define roles like Finance Manager, Sales Rep, Ops Lead. Each role sees only what they need. Assign thousands of users in seconds. Permissions update instantly.
Approval Workflows▾
Invoice over ₹1Cr? Route to CFO. Expense under ₹10K? Auto-approve. Complex rules enforced with mobile approvals and reminders.
Compliance & Audit▾
Every change is recorded. Export trails for audits. Regulatory requirements met with immutable logs.
Unauthorized access eliminated. Fraud prevention via control.
- ✅ Zero unauthorized access
- ✅ Fraud prevention
- ✅ Compliance ready
- ✅ Audit-proof
Every action attributed to a user.
- ✅ User-level tracking
- ✅ Approvals logged
- ✅ Change history
- ✅ Compliance docs
Pricing Plans for Access Control
Access Control is available starting from the Growth plan. Choose the plan that fits your business needs.
*Prices are exclusive of taxes
Growth
For enterprises
/ Month (Billed annually)
Billed yearly- ✓Everything in Startup
- ✓Unlimited Clients & Vendors
- ✓Unlimited Leads & Enquiries
- ✓Unlimited Employees
- ✓Unlimited Assets
- ✓Deals & Contracts
- ✓Employee Spends & Reimbursements
- ✓Email Rules & Tracking
- ✓Unlimited Branches
- ✓Unlimited Warehouses
- ✓Invite upto 5 Teammates
- ✓10 GB Storage Included
- ✓Employee Connect App
- ✓Notekeepr By Upbooks™
- ✓Custom Domain
Enterprise
For large organizations
Talk to our team for a tailored plan
Contact SalesWhat's included:
Questions? We have answers.
Can users have multiple roles?▾
Yes. Assign multiple roles; union of permissions applies.
How do we handle employee offboarding?▾
Deactivate user or auto-deactivate via HR integrations.
Can we integrate with Active Directory?▾
Yes. SSO and directory sync are supported.
What if someone needs temporary access?▾
Grant time-bound access with automatic expiry.
Can we track failed login attempts?▾
Yes. Security events and alerts are available.
How long are audit logs retained?▾
Configurable retention with secure export.
